| 1 Can an electronic banking be secure? |
| 2 Authentication and authorization |
| 3 Rules worth remembering |
| 3.1 Can you trust the computer you use to log in? |
| 3.2 Can anybody see? |
| 3.3 Check the website address, check whether the SSL protocol is used |
| 3.4 Check the server certificate |
| 3.5 Do not share your keys |
| 3.6 Do not share your logging password |
| 3.7 Check logging dates |
| 3.8 Check the image |
| 3.9 Check what you sign |
| 3.10 Log out from the service. |
| 4 What security measures are applied? |
| 4.1 Logging into the system |
| 4.1.1 Masked passwords |
| 4.1.2 Authentication with keys (electronic signature) |
|
4.1.3 Which authentication method to choose?
|
| 4.2 Transaction authorization |
| 4.2.1 Authorization with an electronic signature |
| 4.2.2 Authorization with SMS codes |
| |
| 1 Can an electronic banking be secure? |
Yes, provided that the Internet banking user ensures the computers applied for the Internet banking needs are safe, and observes the rules of the secure usage of such services.
BNP Paribas Bank Polska S.A. has made every effort to develop effective security mechanisms which do not unduly impede the service usage |
 Back Back |
| 2 Authentication and authorization |
To start using the GOonline Biznes system, it is necessary to log into the system. This process is described as authentication. At the moment some operation is to be performed in the system (e.g. a transfer), the system will ask you to confirm this operation, i.e. to authorize the transaction. It constitutes an additional protection against an operation execution by unauthorized persons. This authorizing procedure may be compared to e.g. affixing a signature under a transfer instruction in the branch.
The GOonline Biznes system offers three methods of authentication in the system, which are followed by an appropriate transaction authorization manner:
- Logon using a masked password and an SMS code as well as transaction authorisation with an SMS code
- Logon using a masked password and a token code in reply to the 000000 code entered into the device and the transaction authorisation with the token code in reply to the dedicated six-digit code (other than 000000) entered into the device
- The logon and transaction authorization process with an electronic signature (generated with an USB cryptographic device or a smart card).
More detailed information about authentication and authorization mechanisms applied are available in
section 4.
|
 Back Back |
| 3 Rules worth remembering |
| 3.1 Can you trust the computer you use to log in? |
No security system is fully effective if you can't trust the computer you use to log into the bank. Along with the Internet development new threats have appeared, which a few years ago were yet unknown. Viruses, root kits, Trojan codes, key loggers, phishing, farming, spoofing ... - all these, and other threats not listed here may cause inefficiency of security measures applied. Therefore, regardless of an operating system and web browser you use, take care to:
- secure the computer you use to log on to the GOonline Biznes system as recommended by the operating system's manufacturer,
- install an antivirus software in the system along with up-to-date virus bases,
- make sure the computer is secured as recommended by the manufacturer of the operating system you use.
- install all the patches and updates recommended by the manufacturers of software you are using,
- update the web browser,
- use of software or hardware firewall
Avoid logging on to Internet banking systems from publicly accessible computers, for example in Internet cafés. Do not use public, open WiFi networks.
Why is it so important?
If "malicious" software operates on the computer or in the WiFi network, it may track the connection with the bank, collect passwords you enter, steal your files and even modify the data you enter.
|
 Back Back |
| 3.2 Can anybody see? |
Although the security mechanisms used by the GOonline Biznes system make "looking over a shoulder" an ineffective method of attack, however, it is a good practice to check whether anybody from the environment you work in, shows excessive interest in your activity on the computer.
Why is it so important?
One of the system authentication methods is to log on with an electronic signature. This is a typical example of "something-you-know-and-something-you-have" two-factor authentication. "Something you have" is a private key embedded in the USB device or a smart card, while ?something you know? is the PIN to your USB device or card. It is not easy to guess the PIN as long as it is not trivial. The situation changes when someone reads a valid code over your shoulder. To know one's PIN does not mean to be able to log on to the system, as to do so one must have a private key embedded in the USB device or card.
If you log in using a masked password, while logging in the system demands entering only selected characters from the password, what lowers, but does not eliminate the risk of cracking the password. Then the system will request an additional authorization for the operation with an SMS code, delivered to a predefined telephone number or code from token. Still, logging into the system does not mean a possibility to carry out any operations that require authorization with a code sent in the form of an SMS message. One code authorizes one transaction only.
|
 Back Back |
| 3.3 Check the website address, check whether the SSL protocol is used |
Enter the electronic banking website by typing its full address or use the service link at the bank's websites. Do not use any reference links in electronic messages, or other websites, unless you trust them entirely.
Always check whether the address of the website you've found yourself at is
https://biznesplanet.bnpparibas.pl.
Please verify also whether the connection is initiated using the SSL protocol - in this situation, the address starts with https://. Additionally, web browsers notify about the fact that the initiated connection is a secure one - e.g. through placing a padlock icon on the status bar or through the change of the address bar color.
Why is it so important?
One of password stealing techniques is to provide the website that appears identical to the bank's website. To encourage you to visit that website, you may receive emails in which you will be requested to log in under the provided address to verify the data. The address provided in such emails can be very similar to the genuine address, and so many people may be easily misled in this way. Having the custom to check the website address, you may prevent such fraud attempts.
If data are sent through an unencrypted connection (without using the SSL protocol) it can be intercepted while being sent over the Internet. This is the reason why verification whether the SSL protocol is used is so essential.
|
 Back Back |
| 3.4 Check the server certificate |
Check whether you are actually connecting to the server of BNP Paribas Bank Polska S.A.. It is possible by always verifying the certificate before logging on to the system. To do so, please click the certificate icon that appears after entering the GOonline Biznes address to the browser. Such an icon always shows up when you access encrypted websites i.e. starting with https:// (e.g. a padlock symbol in the Internet Explorer browser)
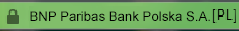
- the certificate has been issued by VeriSign, the trusted certification authority, for BNP Paribas Bank Polska S.A.,
- the certificate has been issued for biznesplanet.bnpparibas.pl and whether it is still valid (to do so, please click Display certificates)
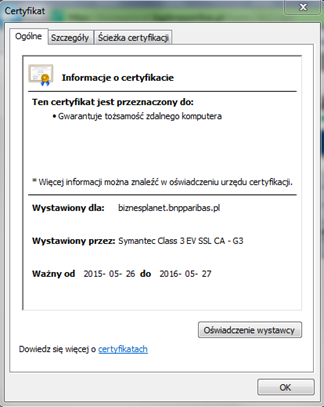
Why is it so important?
Certificate issuance does not require any specialist equipment or software. Anybody may issue on its own a certificate for any domain. In relation to substitution of the website address you may encounter a situation when you connect with a server of a name very similar or even identical to the name of this server, with which you wanted to connect ; you use a encrypted connection, however, it is not this server, but server provided by someone who wants to steal your money. Only verification of the certificate correctness enables you to check whether the server is authentic.
|
 Back Back |
| 3.5 Do not share your keys |
If you use a digital signature option to log on or to authorize transactions, please remember that the Bank does not need your private keys - you are the only person who should have access to such keys. You will never be asked by the Bank for your USB cryptographic device, smart card or PIN to them. Please remember that both the cryptographic device and smart card are required only at the moment when the window for selecting authorisation key pops up. After entering a password and executing transactions, devices should be disconnected / the card should be removed from the reader.
Never leave your USB cryptographic device or card unattended, avoid trivial PINs and try not to take down such PINs. If you must write down your PIN, do not keep it together with your USB device or card.
Why is it so important?
A private key allows you to log on to the Internet banking system and authorize operations performed in the system. If any other person has your private key, s/he could try to carry out operations on your behalf.
However, if you use a token, please remember that the device has been assigned by the Bank to a specific user and it should not be provided available to any third parties. To separate the logon from authorisation of instructions, the Bank has differentiated the codes to be entered depending on the action: to log on, the user is always requested to enter 000000 (six zeros), while for authorisation purposes, dedicated six digits that are displayed on the signature form should be entered.
|
 Back Back |
| 3.6 Do not share your logging password |
If you log in using a masked password, while logging you have to enter only some characters from your password. Remember that the bank never needs your entire password, except for a case of changing it to the new password. The password (in a masked form) is only used while logging into the electronic banking system, nowhere else in the system, nor outside the system, it is required.
Why is it so important?
It happens that frauds ask the bank customers to enter their passwords for ostensible verification. This way they acquire customer passwords which could be used to access the customer accounts.
|
 Back Back |
| 3.7 Check logging dates |
After logging to the system, check the last logging dates, both the successful and unsuccessful attempts. If the dates are different from what you remember to be, this should arouse your concern. You can contact the bank to explain the doubts.
Why is it so important?
If the last logging date is different from what you remember to be, it probably means that someone accessed your account. In such a situation you should contact the bank to explain the situation. Unsuccessful logging attempts unrelated to your actions may show that someone was trying to crack your password.
|
 Back Back |
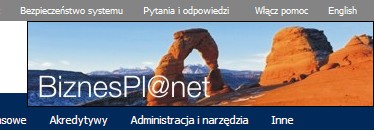
| 3.8 Check the image |
One of the website graphic features is the image, which you can customize. If the image displayed is not the one you have selected it may mean that the website you are reviewing is not the genuine bank's website. In such a case you should refrain from performing any operation until the doubts are dissolved.
Why is it so important?
The digital certificate allows you to verify whether the connection has been initiated with the appropriate server. Certificate verification may be difficult, thus, to facilitate it, a customized image was added, which is easier to recognize. Remember, however, that the image verification should not be used instead of the server certificate's verification.
|
 Back Back |
| 3.9 Check what you sign |
External operations carried out in the Internet banking service must be confirmed by you through appending an electronic signature or entering a code sent via text message (SMS). Always remember to check the data presented in the form for signing an instruction.
If you use the transaction authorisation method with SMS codes, before signing any instruction, please make sure that the operation details contained in the authorisation SMS code comply with the data you have entered in the system. Please compare the date with e.g. an invoice or another document. Pay special attention to the beneficiary's account number and transaction amount. If you use the transaction authorisation method with an electronic signature, before signing any instruction please make sure that the operation details displayed when signing the instruction comply with the data you entered in the system. Please compare the date with e.g. an invoice or another document. Pay special attention to the beneficiary's account number and transaction amount.
Why is it so important?
Signing of an instruction confirms all its parameters, including the amount and target account. In case of an infected computer, it may happen that the data entered at the beginning of transfer execution would be modified before sending to a signing component. Therefore, a repeated verification of data before confirming the instruction is so important.
|
 Back Back |
| 3.10 Log out from the service. |
When you finish to use the electronic banking service, always log out from it through selecting an appropriate option. Although it is not necessary, you may also close all web browser windows. To be on the safe side, you can do it on public computers. Never leave a computer with an initiated session in the electronic banking system unattended.
Why is it so important?
Logging into the service you initiate so called session. It ends in the moment you select logging out option, close a web browser or upon the lapse of a given inactive time limit. If the session is not closed, someone might use it to make operations on your bank account.
|
 Back Back |
| 4 What security measures are applied? |
| 4.1 Logging into the system |
To start using the GOonline Biznes system, it is necessary to log on to the system. In this process, called authentication, it is verified whether the person logging on is the person as whom he/she poses.
The GOonline Biznes system supports two logon methods:
- Logon with a masked password and SMS code
In order to log in to the system, please provide your user name (login) and then type the demanded password characters. Providing only selected characters is one of security mechanisms. In case of password interception attempts, only some characters are intercepted. At the subsequent logon, the system will require typing other characters from the password
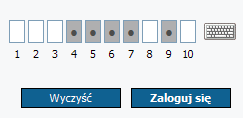
Then the system will display a form with a field to enter a one-off SMS code (delivered to the predefined telephone number).
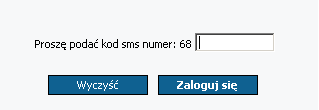
Moreover, a separate SMS code is generated to each operation that requires authorisation.
- Logon using a masked password and a token code (upon entering 000000)
In order to log in to the system, please provide your user name (login) and then type the demanded password characters. Providing only selected characters is one of security mechanisms. In case of password interception attempts, only some characters are intercepted. At the subsequent logon, the system will require typing other characters from the password

Then the system will display a form with a field to enter a token code for the 000000 number.

Moreover, a separate token code is generated to each operation that requires authorisation.
- Logowanie podpisem elektronicznym
In order to log on to the system, provide your user name (login) and then sign with the electronic signature, which consists in indicating a private key and typing the PIN to the carrier where the key is stored. Keys for the signature can be generated on USB cryptographic carrier or smart cards.
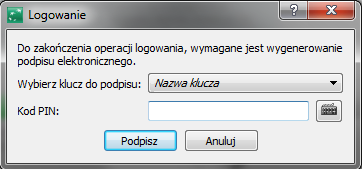
Passwords can be entered using a standard keyboard or selecting respective characters from the virtual keyboard which will be displayed upon clicking its icon. The virtual keyboard is a security measure against the interception of passwords typed on the standard keyboard.
Both methods ensure an appropriate security level provided that the rules of conduct discussed here are observed. You should also remember that the authentication method determines the manner of transaction authorization.
|
 Back Back |
| 4.1.1 Masked passwords |
A masked password is a password, from which you must enter only password characters demanded by the system while logging. As a result, even if somebody spies on characters entered by you, he/ she will not get to know your entire password, but only its part. However, remember that if somebody will spy on you for a longer time, or there is a spying software operating on the computer you use for logging that records the characters entered, with time your entire password will be known. This is the reason why the password should be change from time to time, in particular, if it was used in a situation when somebody could spy it on or the computer used was not a reliable one.
The advantage of a masked password is that you don't have to carry with you an encrypting card or other carrier with your private key. It also doesn't require installation of any additional components on the computer you use.
The bank does not store the full form of your masked password. The only moment the password appears in the system in its full form is the process of its change. During this operation the system generates a definite number of masks, which will be next used in the process of the user authentication. For each of these masks an abbreviation of a corresponding password part is saved in the base. As a result when later the user authentication is performed, the system may verify whether s/he entered a correct password, without a need to store the password in an open form in the base.
Remember that choosing a masked password as an authentication method simultaneously results in using SMS or Vasco token codes in the process of logon or orders authorization.
|
 Back Back |
| 4.1.2 Authentication with keys (electronic signature) |
Authentication method by e-signature is based on asymmetric cryptography (Public-key cryptography). In authentication process, the system verifies whether a person logging in has a valid private key and knows the PIN code securing a cryptographic device storing the key (smart card device).
A private key used in the authentication process may be stored on a smart card or a USB cryptographic device.
An encrypting card is a plastic element of a credit card size with an embedded microprocessor. A private key is stored in the chip memory on the card, encrypting operations are carried out by the card microprocessor. An access to the keys stored on the card is protected with a PIN code, keys are generated on the card, a private key is never available outside the card.
USB cryptographic devices work in a similar way. An USB cryptographic device resembles a pen-drive. What differs an USB device from a smart card is that USB devices do not require an additional reader (you connect them directly to the computer). A private key, as in the case of a smart card, is saved in the on-chip memory.
Please note that to get authenticated with the keys you must:
- install on your computer components that execute the process (administrator rights may be required on a given computer),
- also have a reader if you use a smart card,
- carry an USB cryptographic device or a smart card where the keys are saved.
Remember that choosing an electronic signature as an authentication method simultaneously results in using an electronic signature in the process of order authorization.
|
 Back Back |
| 4.1.3 Which authentication/authorization method to choose? |
If you use only your own computer, have a cryptographic card reader or you can buy it, you may choose the logon with the use of keys stored on a cryptographic card. Then you have to protect your card and its PIN.
If you use several computers where you could install the components necessary to digitally sign in the GOonline Biznes system, you may chose the e-signature option to authenticate, and use the USB cryptographic device as a data carrier. The key embedded in the USB device, like in the case of a smart card, is secured with a PIN.
If you use different computers, including such where you could not be able to install the components necessary to append an electronic signature, if you do not wish to carry a USB cryptographic device or a smart card and a card reader, but you always have your mobile phone with you, you may choose to use the masked password and SMS code options.
|
 Back Back |
| 4.2 Transaction authorization |
|
Transaction authorization aims at confirming operations ordered by an authenticated user. This is an additional security measure that prevents anybody from withdrawing money from your account even if he/ she gets to know your logging password.
|
 Back Back |
| 4.2.1 Authorization with an electronic signature |
|
If you use an electronic signature, on the basis of all transaction elements a unique value (encryption shortcut) is calculated. The shortcut is signed using the user's private key and sent to a server. On the server's side the operation of calculating a encryption shortcut is repeated on the basis of transaction parameters received by the server, and then the consumer's signature under the shortcut received is verified. If the signature is correct, the transaction is executed.
|
 Back Back |
| 4.2.2 Authorization with SMS codes |
|
As regards SMS codes, each time a different SMS code is used to confirm a transaction. In typical implementations of this transaction authorization method a single-use code, which is not related to transaction parameters, is sent directly to the server along with other operation parameters. In the GOonline Biznes system, to increase its security, the password is not sent to the server. Instead, an authorization code, which connects transaction parameters with a valid single-use password, is sent. An authorization code is calculated with the HMAC algorithm. The server verifies whether the code sent is correct, if it is a proper one, the transaction is executed.
|
 Back Back |